
How Hackers Use Tunneling to Bypass Any Firewall (Red Team Playbook)
Picture this: a fortress with towering walls, guarded gates, and watchful sentries. That’s your network firewall. […]

Government considered destroying its data hub after decade-long intrusion
A Chinese-sponsored cyber attack was so damaging that it was briefly proposed that an entire data […]

North Korean threat actors turn blockchains into malware delivery servers
Nation-state threat actors and cybercriminals are increasingly abusing cryptocurrency blockchains to host malicious payloads with a […]
Sora 2 Update: OpenAI Adds Longer Clips and Frame-by-Frame Storyboarding
OpenAI’s Sora 2 is getting a blockbuster upgrade — longer, more structured AI videos and a […]
Spotify Partners With Major Labels to Build Artist-First AI Music Products
Spotify is deepening its role in shaping the future of music technology, announcing that it will […]
Waymo Robotaxis Coming to London
Waymo announced on Wednesday an expansion of its self-driving operation to London in 2026, the company’s […]
Salesforce Unveils Agentforce AI-Powered Humanoid Robot ‘Henry’
Salesforce has given its AI a body. Meet Henry, a humanoid robot powered by the company’s […]
Alibaba Claims AI E-Commerce Tools Already Pay for Themselves”
Alibaba Group said its investment in artificial intelligence has reached break-even levels within its e-commerce business. […]
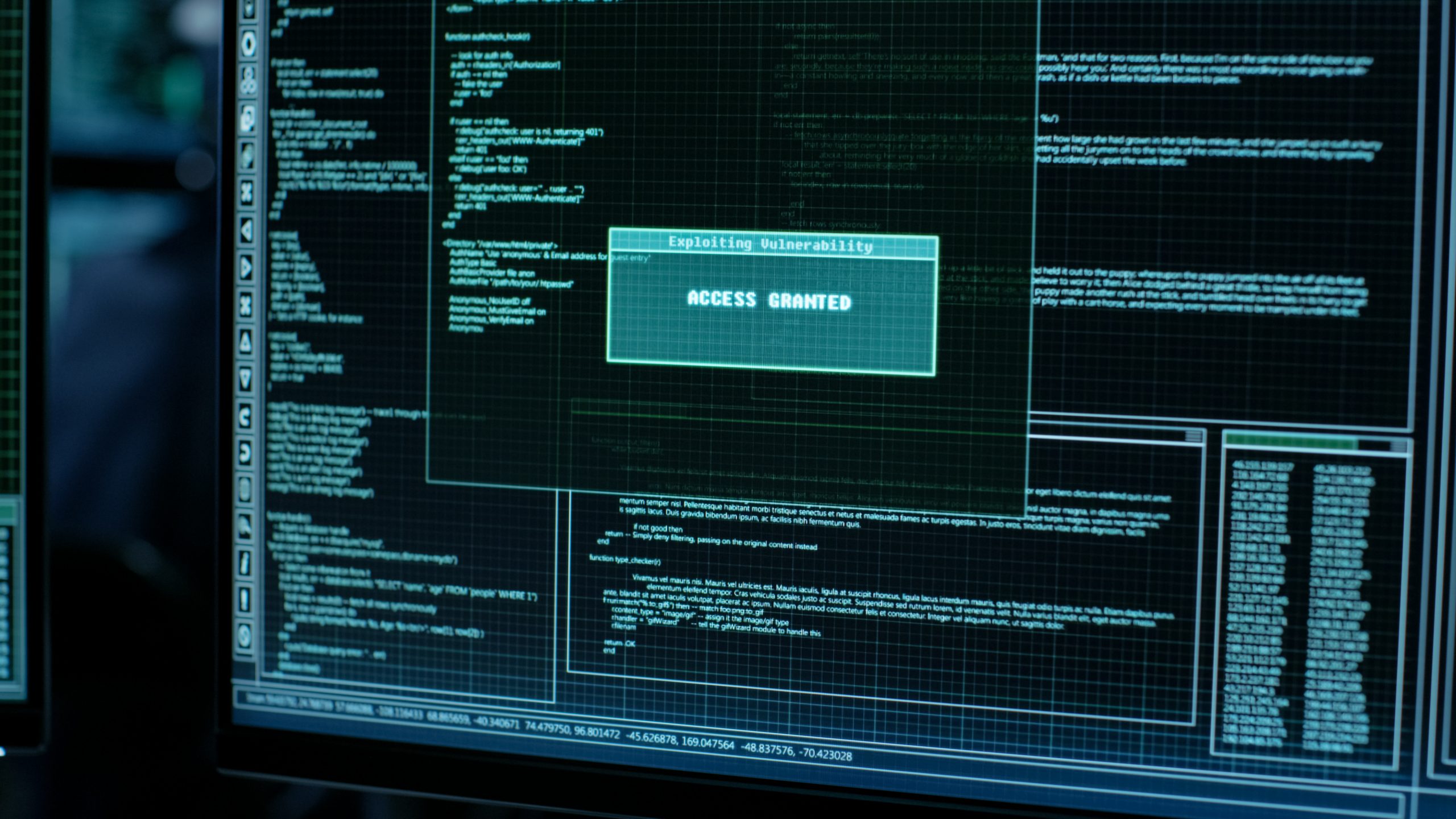
Critical ASP.NET core vulnerability earns Microsoft’s highest-ever severity score
Microsoft has patched a critical vulnerability in ASP.NET Core that earned a CVSS severity score of […]

‘Zero Disco’ campaign hits legacy Cisco switches with fileless rootkit payloads
In newly disclosed real-world attacks, threat actors are found exploiting a Cisco Simple Network Management Protocol […]
